| Skip Navigation Links | |
| Exit Print View | |

|
Oracle Solaris 11.1 Administration: Security Services Oracle Solaris 11.1 Information Library |
| Skip Navigation Links | |
| Exit Print View | |

|
Oracle Solaris 11.1 Administration: Security Services Oracle Solaris 11.1 Information Library |
1. Security Services (Overview)
Part II System, File, and Device Security
2. Managing Machine Security (Overview)
3. Controlling Access to Systems (Tasks)
4. Virus Scanning Service (Tasks)
5. Controlling Access to Devices (Tasks)
6. Verifying File Integrity by Using BART (Tasks)
7. Controlling Access to Files (Tasks)
Part III Roles, Rights Profiles, and Privileges
8. Using Roles and Privileges (Overview)
9. Using Role-Based Access Control (Tasks)
10. Security Attributes in Oracle Solaris (Reference)
Part IV Cryptographic Services
11. Cryptographic Framework (Overview)
12. Cryptographic Framework (Tasks)
Part V Authentication Services and Secure Communication
14. Using Pluggable Authentication Modules
17. Using Simple Authentication and Security Layer
18. Network Services Authentication (Tasks)
19. Introduction to the Kerberos Service
20. Planning for the Kerberos Service
21. Configuring the Kerberos Service (Tasks)
22. Kerberos Error Messages and Troubleshooting
23. Administering Kerberos Principals and Policies (Tasks)
24. Using Kerberos Applications (Tasks)
25. The Kerberos Service (Reference)
Part VII Auditing in Oracle Solaris
Rights Profiles for Administering Auditing
Auditing and Oracle Solaris Zones
Audit Configuration Files and Packaging
Audit Policies for Asynchronous and Synchronous Events
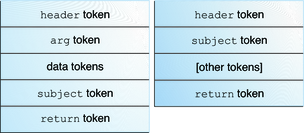
An audit record is a sequence of audit tokens. Each audit token contains event information such as user ID, time, and date. A header token begins an audit record, and an optional trailer token concludes the record. Other audit tokens contain information relevant to the audit event. The following figure shows a typical kernel audit record and a typical user-level audit record.
Figure 29-1 Typical Audit Record Structures
Audit record analysis involves post-selecting records from the audit trail. You can use one of two approaches to parsing the binary data that was collected.
You can use the praudit command. Options to the command provide different text output. For example, the praudit -x command provides XML for input into scripts and browsers. praudit output does not include fields whose sole purpose is to help to parse the binary data. Note that the order and format of praudit output is not guaranteed between Oracle Solaris releases.
For examples of praudit output, see How to View the Contents of Binary Audit Files.
For examples of praudit output for each audit token, see the individual tokens in Audit Token Formats.
You can write a program to parse the binary data stream. The program must take into account the variants of an audit record. For example, the ioctl() system call creates an audit record for “Bad file name”. This record contains different tokens from the ioctl() audit record for “Invalid file descriptor”.
For a description of the order of binary data in each audit token, see the audit.log(4) man page.
For manifest values, see the /usr/include/bsm/audit.h file.
To view the order of tokens in an audit record, use the auditrecord command. Output from the auditrecord command includes the different tokens for different manifest values. Square brackets ([]) indicate that an audit token is optional. For more information, see the auditrecord(1M) man page.