| Skip Navigation Links | |
| Exit Print View | |

|
Oracle Solaris 11.1 Administration: Security Services Oracle Solaris 11.1 Information Library |
| Skip Navigation Links | |
| Exit Print View | |

|
Oracle Solaris 11.1 Administration: Security Services Oracle Solaris 11.1 Information Library |
1. Security Services (Overview)
Part II System, File, and Device Security
2. Managing Machine Security (Overview)
3. Controlling Access to Systems (Tasks)
4. Virus Scanning Service (Tasks)
5. Controlling Access to Devices (Tasks)
6. Verifying File Integrity by Using BART (Tasks)
7. Controlling Access to Files (Tasks)
Part III Roles, Rights Profiles, and Privileges
8. Using Roles and Privileges (Overview)
9. Using Role-Based Access Control (Tasks)
10. Security Attributes in Oracle Solaris (Reference)
Part IV Cryptographic Services
11. Cryptographic Framework (Overview)
12. Cryptographic Framework (Tasks)
Part V Authentication Services and Secure Communication
14. Using Pluggable Authentication Modules
Planning for Your PAM Implementation
How to Prevent Rhost-Style Access From Remote Systems With PAM
How to Assign a Customized PAM Policy to a User
How to Assign a New Rights Policy to All Users
PAM Configuration Search Order
Per User Authentication Policy
17. Using Simple Authentication and Security Layer
18. Network Services Authentication (Tasks)
19. Introduction to the Kerberos Service
20. Planning for the Kerberos Service
21. Configuring the Kerberos Service (Tasks)
22. Kerberos Error Messages and Troubleshooting
23. Administering Kerberos Principals and Policies (Tasks)
24. Using Kerberos Applications (Tasks)
25. The Kerberos Service (Reference)
The Pluggable Authentication Module (PAM) framework lets you “plug in” new authentication services without changing system services, such as login, su, and ssh. You can also use PAM to integrate UNIX login with other security mechanisms such as Kerberos. Mechanisms for account, credential, session, and password management can also be “plugged in” by using this framework.
The PAM framework enables you to configure the use of system services (such as, su, login, or ssh) for user authentication. Some benefits that PAM provides are as follows:
Flexible configuration policy
Per-application authentication policy
Per-user authentication policy
The ability to choose a default authentication mechanism
The ability to require multiple authorizations on high-security systems
Ease of use for the end user
No retyping of passwords if the passwords are the same for different authentication services
The ability to prompt the user for passwords for multiple authentication services without requiring the user to type multiple commands
The ability to pass options to the user authentication services
The ability to implement a site-specific security policy without having to change the system entry services
The PAM framework consists of four parts:
PAM consumers
PAM library
PAM configuration
PAM service modules, also referred to as providers
The framework provides a uniform way for authentication-related activities to take place. This approach enables application developers to use PAM services without having to know the semantics of the policy. Algorithms are centrally supplied. The algorithms can be modified independently of the individual applications. With PAM, administrators can tailor the authentication process to the needs of a particular system without having to change any applications. Adjustments are made through the PAM configuration.
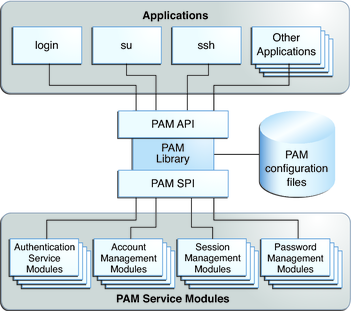
The following figure illustrates the PAM architecture. Applications communicate with the PAM library through the PAM application programming interface (API). PAM modules communicate with the PAM library through the PAM service provider interface (SPI). Thus, the PAM library enables applications and modules to communicate with each other.
Figure 14-1 PAM Architecture
The PAM framework included in the Oracle Solaris 11.1 release includes several new features including:
definitive control flag
per-service configuration
per-user configuration