| Skip Navigation Links | |
| Exit Print View | |

|
Oracle Solaris 11.1 Administration: Security Services Oracle Solaris 11.1 Information Library |
| Skip Navigation Links | |
| Exit Print View | |

|
Oracle Solaris 11.1 Administration: Security Services Oracle Solaris 11.1 Information Library |
1. Security Services (Overview)
Part II System, File, and Device Security
2. Managing Machine Security (Overview)
3. Controlling Access to Systems (Tasks)
4. Virus Scanning Service (Tasks)
5. Controlling Access to Devices (Tasks)
6. Verifying File Integrity by Using BART (Tasks)
7. Controlling Access to Files (Tasks)
Part III Roles, Rights Profiles, and Privileges
8. Using Roles and Privileges (Overview)
9. Using Role-Based Access Control (Tasks)
10. Security Attributes in Oracle Solaris (Reference)
Part IV Cryptographic Services
11. Cryptographic Framework (Overview)
Terminology in the Cryptographic Framework
Scope of the Cryptographic Framework
Administrative Commands in the Cryptographic Framework
User-Level Commands in the Cryptographic Framework
Binary Signatures for Third-Party Software
Plugins to the Cryptographic Framework
Cryptographic Services and Zones
Cryptographic Framework and FIPS-140
Cryptographic Framework and the SPARC T-Series Servers in This Release
12. Cryptographic Framework (Tasks)
Part V Authentication Services and Secure Communication
14. Using Pluggable Authentication Modules
17. Using Simple Authentication and Security Layer
18. Network Services Authentication (Tasks)
19. Introduction to the Kerberos Service
20. Planning for the Kerberos Service
21. Configuring the Kerberos Service (Tasks)
22. Kerberos Error Messages and Troubleshooting
23. Administering Kerberos Principals and Policies (Tasks)
24. Using Kerberos Applications (Tasks)
25. The Kerberos Service (Reference)
The Cryptographic Framework provides a common store of algorithms and PKCS #11 libraries to handle cryptographic requirements. The PKCS #11 libraries are implemented according to the following standard: RSA Security Inc. PKCS #11 Cryptographic Token Interface (Cryptoki).
Figure 11-1 Cryptographic Framework Levels
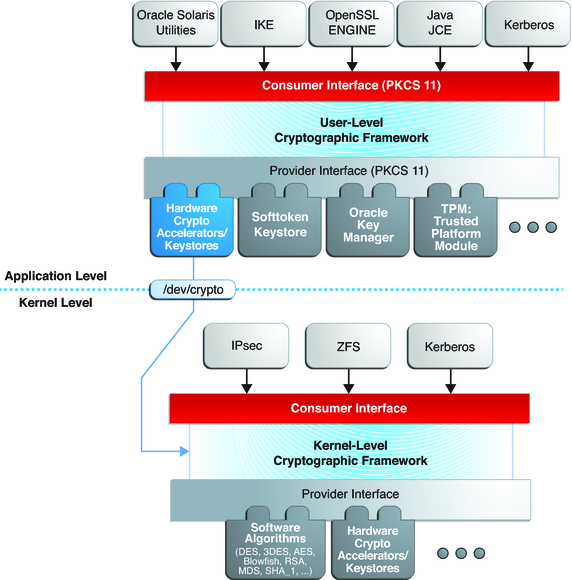
At the kernel level, the framework currently handles cryptographic requirements for Kerberos and IPsec. User-level consumers include libsasl and IKE. The kernel SSL (kssl) proxy uses the Cryptographic Framework. For more information, see SSL Kernel Proxy Encrypts Web Server Communications in Securing the Network in Oracle Solaris 11.1 and the ksslcfg(1M) man page.
Export law in the United States requires that the use of open cryptographic interfaces be licensed. The Cryptographic Framework satisfies the current law by requiring that kernel cryptographic providers and PKCS #11 cryptographic providers be signed. For further discussion, see Binary Signatures for Third-Party Software.
The framework enables providers of cryptographic services to have their services used by many consumers in Oracle Solaris. Another name for providers is plugins. The framework allows three types of plugins:
User-level plugins – Shared objects that provide services by using PKCS #11 libraries, such as pkcs11_softtoken.so.1.
Kernel-level plugins – Kernel modules that provide implementations of cryptographic algorithms in software, such as AES.
Many of the algorithms in the framework are optimized for x86 with the SSE2 instruction set and for SPARC hardware.
Hardware plugins – Device drivers and their associated hardware accelerators. The Niagara chips, the ncp and n2cp device drivers, are one example. A hardware accelerator offloads expensive cryptographic functions from the operating system. The Sun Crypto Accelerator 6000 board is one example.
The framework implements a standard interface, the PKCS #11, v2.20 amendment 3 library, for user-level providers. The library can be used by third-party applications to reach providers. Third parties can also add signed libraries, signed kernel algorithm modules, and signed device drivers to the framework. These plugins are added when the pkgadd utility installs the third-party software. For a diagram of the major components of the framework, see Chapter 8, Introduction to the Oracle Solaris Cryptographic Framework, in Developer’s Guide to Oracle Solaris 11 Security.