| Skip Navigation Links | |
| Exit Print View | |

|
Trusted Extensions Configuration and Administration Oracle Solaris 11.1 Information Library |
| Skip Navigation Links | |
| Exit Print View | |

|
Trusted Extensions Configuration and Administration Oracle Solaris 11.1 Information Library |
Part I Initial Configuration of Trusted Extensions
1. Security Planning for Trusted Extensions
2. Configuration Roadmap for Trusted Extensions
3. Adding the Trusted Extensions Feature to Oracle Solaris (Tasks)
4. Configuring Trusted Extensions (Tasks)
5. Configuring LDAP for Trusted Extensions (Tasks)
Part II Administration of Trusted Extensions
6. Trusted Extensions Administration Concepts
7. Trusted Extensions Administration Tools
8. Security Requirements on a Trusted Extensions System (Overview)
9. Performing Common Tasks in Trusted Extensions
10. Users, Rights, and Roles in Trusted Extensions (Overview)
11. Managing Users, Rights, and Roles in Trusted Extensions (Tasks)
12. Remote Administration in Trusted Extensions (Tasks)
13. Managing Zones in Trusted Extensions
14. Managing and Mounting Files in Trusted Extensions
15. Trusted Networking (Overview)
Trusted Extensions Data Packets
Trusted Extensions Multicast Packets
Trusted Network Communications
Network Commands in Trusted Extensions
Network Configuration Databases in Trusted Extensions
Trusted Network Security Attributes
Network Security Attributes in Trusted Extensions
Host Type and Template Name in Security Templates
Default Label in Security Templates
Domain of Interpretation in Security Templates
Label Range in Security Templates
Auxiliary Labels in Security Templates
Trusted Network Fallback Mechanism
Overview of Routing in Trusted Extensions
Routing Table Entries in Trusted Extensions
Trusted Extensions Accreditation Checks
Destination Accreditation Checks
Administration of Routing in Trusted Extensions
Choosing Routers in Trusted Extensions
Administration of Labeled IPsec
Labels for IPsec-Protected Exchanges
Label Extensions for IPsec Security Associations
Labels and Accreditation in Tunnel Mode IPsec
Confidentiality and Integrity Protections With Label Extensions
16. Managing Networks in Trusted Extensions (Tasks)
17. Trusted Extensions and LDAP (Overview)
18. Multilevel Mail in Trusted Extensions (Overview)
19. Managing Labeled Printing (Tasks)
20. Devices in Trusted Extensions (Overview)
21. Managing Devices for Trusted Extensions (Tasks)
22. Trusted Extensions Auditing (Overview)
23. Software Management in Trusted Extensions
Creating and Managing a Security Policy
Site Security Policy and Trusted Extensions
Computer Security Recommendations
Physical Security Recommendations
Personnel Security Recommendations
Additional Security References
B. Configuration Checklist for Trusted Extensions
Checklist for Configuring Trusted Extensions
C. Quick Reference to Trusted Extensions Administration
Administrative Interfaces in Trusted Extensions
Oracle Solaris Interfaces Extended by Trusted Extensions
Tighter Security Defaults in Trusted Extensions
Limited Options in Trusted Extensions
D. List of Trusted Extensions Man Pages
Trusted Extensions Man Pages in Alphabetical Order
Oracle Solaris Man Pages That Are Modified by Trusted Extensions
Trusted Extensions supports several methods for routing communications between networks. You can set up routes that enforce the degree of security that your site's security policy requires.
For example, sites can restrict communications outside the local network to a single label. This label is applied to publicly available information. Labels such as UNCLASSIFIED or PUBLIC can indicate public information. To enforce the restriction, these sites add the gateway's network interface that is connected to the external network to a single-label template. For more details about TCP/IP and routing, see the following:
Configuring an IPv4 Router in Configuring and Administering Oracle Solaris 11.1 Networks
netcfg(1M) man page
Trusted Extensions hosts offer the highest degree of trust as routers. Other types of routers might not recognize Trusted Extensions security attributes. Without administrative action, packets can be routed through routers that do not provide MAC security protection.
Labeled routers drop packets when they do not find the correct type of information in the IP options section of the packet. For example, a labeled router drops a packet if it does not find a labeled option in the IP options when the option is required, or when the DOI in the IP options is not consistent with the destination's accreditation.
Other types of routers that are not running Trusted Extensions software can be configured to either pass the packets or drop the packets that include a labeled option. Only label-aware gateways such as Trusted Extensions can use the contents of the CALIPSO or CIPSO IP option to enforce MAC.
To support trusted routing, the routing tables are extended to include Trusted Extensions security attributes. The attributes are described in Routing Table Entries in Trusted Extensions. Trusted Extensions supports static routing, in which the administrator creates routing table entries manually. For details, see the -p option in the route(1M) man page.
The routing software tries to find a route to the destination host in the routing tables. When the host is not explicitly named, the routing software looks for an entry for the subnet where the host resides. When neither the host nor the subnet is defined, the host sends the packet to a default gateway, if defined. Multiple default gateways can be defined, and each is treated equally.
In this release of Trusted Extensions, the security administrator sets up routes manually, and then manually changes the routing table when conditions change. For example, many sites have a single gateway that communicates with the outside world. In these cases, the single gateway can be statically defined as the default on each host on the network.
An example of routing in Trusted Extensions follows. The diagram and table show three potential routes between Host 1 and Host 2.
Figure 15-1 Typical Trusted Extensions Routes and Routing Table Entries
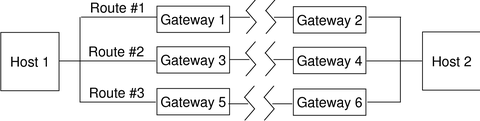
|
Route #1 can transmit packets within the label range of CONFIDENTIAL to SECRET.
Route #2 can transmit packets from ADMIN_LOW to ADMIN_HIGH.
Route #3 does not specify routing information. Therefore, its security attributes are derived from Gateway 5's security template.
To display labels and extended security attributes for sockets, Trusted Extensions modifies the following Oracle Solaris network commands:
The netstat -rR command displays the security attributes in routing table entries.
The netstat -aR command displays the security attributes for sockets.
The route -p command with the add or delete option changes the routing table entries.
For details, see the netstat(1M) and route(1M) man pages.
To change routing table entries, Trusted Extensions provides the following interfaces:
The txzonemgr GUI can be used to assign the default route for an interface.
The route -p command with the add or delete option can be used to change routing table entries.
For examples, see How to Add Default Routes.