| Skip Navigation Links | |
| Exit Print View | |
|
Resource Management, Oracle Solaris Zones, and Oracle Solaris 10 Zones Developer's Guide Oracle Solaris 11.1 Information Library |
| Skip Navigation Links | |
| Exit Print View | |
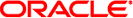
|
Resource Management, Oracle Solaris Zones, and Oracle Solaris 10 Zones Developer's Guide Oracle Solaris 11.1 Information Library |
1. Resource Management in the Oracle Solaris Operating System
3. Using the C Interface to Extended Accounting
4. Using the Perl Interface to Extended Accounting
Resource Controls Flags and Actions
Resource Control Values and Privilege Levels
Global Actions and Global Flags
Resource Control Sets Associated With a Zone, Project, Processes, and Tasks
Resource Controls Associated With a Project
Resource Controls Associated With Tasks
Resource Controls API Functions
Operate on Action-Value Pairs of a Resource Control
Operate on Local Modifiable Values
Retrieve Local Read-Only Values
Retrieve Global Read-Only Actions
Resource Control Code Examples
Master Observing Process for Resource Controls
List all the Value-Action Pairs for a Specific Resource Control
Set project.cpu-shares and Add a New Value
Set LWP Limit Using Resource Control Blocks
Programming Issues Associated With Resource Controls
zonestat Utility for Monitoring Zones Resource Usage
7. Design Considerations for Resource Management Applications in Oracle Solaris Zones
This section describes flags, actions, and signals associated with resource controls.
rlimit is process-based. rlimit establishes a restricting boundary on the consumption of a variety of system resources by a process. Each process that the process creates inherits from the original process. A resource limit is defined by a pair of values. The values specify the current (soft) limit and the maximum (hard) limit.
A process might irreversibly lower its hard limit to any value that is greater than or equal to the soft limit. Only a process with root ID can raise the hard limit. See setrlimit() and getrlimit().
The rlimit structure contains two members that define the soft limit and hard limit.
rlim_t rlim_cur; /* current (soft) limit */ rlim_t rlim_max /* hard limit */
rctl extends the process-based limits of rlimit by controlling resource consumption by processes, tasks, and projects defined in the project database.
Note - The rctl mechanism is preferred to the use of rlimit to set resource limits. The only reason to use the rlimit facility is when portability is required across UNIX platforms.
Applications fall into the following broad categories depending on how an application deals with resource controls. Based on the action that is taken, resource controls can be further classified. Most report an error and terminate operation. Other resource controls allow applications to resume operation and adapt to the reduced resource usage. A progressive chain of actions at increasing values can be specified for each resource control.
The list of attributes for a resource control consists of a privilege level, a threshold value, and an action that is taken when the threshold is exceeded.
Each threshold value on a resource control must be associated with one of the following privilege levels:
Privilege level can be modified by the owner of the calling process. RCPRIV_BASIC is associated with a resource's soft limit.
Privilege level can be modified only by privileged (root) callers. RCPRIV_PRIVILEGED is associated with a resource's hard limit.
setrctl(2) will only succeed when called as a privileged user in the global zone. Inside a non-global zone, root cannot set zone-wide controls.
Privilege level remains fixed for the duration of the operating system instance.
Figure 5-2 shows the timeline for setting privilege levels for signals that are defined by the /etc/project file process.max-cpu-time resource control.
The local action and local flags are applied to the current resource control value represented by this resource control block. Local actions and local flags are value-specific. For each threshold value that is placed on a resource control, the following local actions and local flags are available:
No local action is taken when this resource control value is exceeded.
The specified signal, set by rctlblk_set_local_action(), is sent to the process that placed this resource control value in the value sequence.
When this resource control value is encountered, the request for the resource is denied. Set on all values if RCTL_GLOBAL_DENY_ALWAYS is set for this control. Cleared on all values if RCTL_GLOBAL_DENY_NEVER is set for this control.
This resource control value represents a request for the maximum amount of resource for this control. If RCTL_GLOBAL_INFINITE is set for this resource control, RCTL_LOCAL_MAXIMAL indicates an unlimited resource control value that is never exceeded.
Global flags apply to all current resource control values represented by this resource control block. Global actions and global flags are set by rctladm(1M). Global actions and global flags cannot be set with setrctl(). Global flags apply to all resource controls. For each threshold value that is placed on a resource control, the following global actions and global flags are available:
No global action is taken when a resource control value is exceeded on this control.
A standard message is logged by the syslog() facility when any resource control value on a sequence associated with this control is exceeded.
Defines the unit string of the limit value as seconds.
Defines the unit string of the limit value as count.
Defines the unit string of the limit value as bytes.
Flag means that RCTL_GLOBAL_SYSLOG cannot be set for this resource control through rctladm(1M).
No values with the RCPRIV_BASIC privilege are permitted on this control.
Non-privileged callers are able to lower the value of privileged resource control values on this control.
The action that is taken when a control value is exceeded on this control always includes denial of the resource.
The action that is taken when a control value is exceeded on this control always excludes denial of the resource. The resource is always granted, although other actions can also be taken.
The valid signals for local actions include the SIGXFSZ signal.
The valid signals for local actions include the SIGXCPU signal.
No local actions are permitted on this control. The resource is always granted.
This resource control supports the concept of an unlimited value. Generally, an unlimited value applies only to accumulation-oriented resources, such as CPU time.
Generally, a task or project related resource control does not support observational control values. An RCPRIV_BASIC privileged control value placed on a task or process generates an action only if the value is exceeded by the process that placed the value.
The following figure shows the resource control sets associated with zones, tasks, processes and a project.
Figure 5-1 Resource Control Sets for Zone, Task, Project, and Process
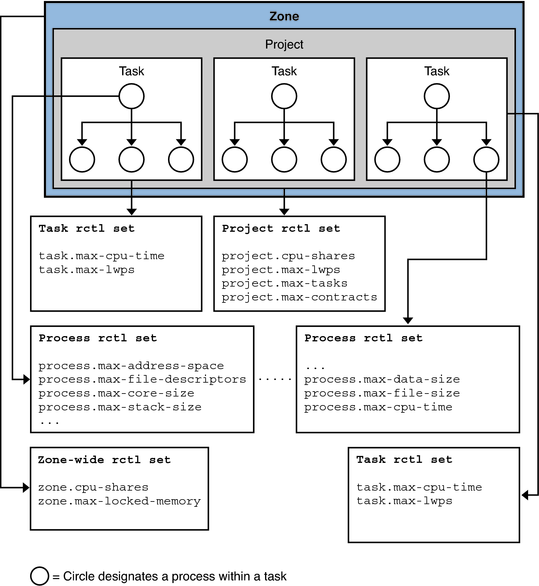
More than one resource control can exist on a resource, each resource control at a containment level in the process model. Resource controls can be active on the same resource for both a process and collective task or collective project. In this case, the action for the process takes precedence. For example, action is taken on process.max-cpu-time before task.max-cpu-time if both controls are encountered simultaneously.
Resource controls associated with a project include the following:
Absolute limit on the amount of CPU resources that can be consumed by a project. A value of 100 means 100 percent of one CPU as the project.cpu-cap setting. A value of 125 is 125 percent, because 100 percent corresponds to one full CPU on the system when using CPU caps.
The number of CPU shares that are granted to this project for use with the fair share scheduler, FSS(7).
Total amount of kernel memory that can be used by libpkcs11 for hardware crypto acceleration. Allocations for kernel buffers and session-related structures are charged against this resource control.
Total amount of physical locked memory allowed.
Note that this resource control replaced project.max-device-locked-memory, which has been removed.
Maximum number of System V message queues allowed for a project.
Maximum allowable number of event ports.
Maximum number of process table slots simultaneously available to this project.
Note - Both normal processes and zombie processes take up process table slots. The max-processes resource control thus protects against zombie processes exhausting the process table. Note that max-lwps cannot protect against zombie processes exhausting the process table since zombie processes do not have any LWPs by definition.
Maximum number of semaphore IDs allowed for a project.
Maximum number of shared memory IDs allowed for this project.
Maximum number of message queue IDs allowed for this project.
Total amount of System V shared memory allowed for this project.
Maximum number of LWPs simultaneously available to this project.
Maximum number of tasks allowable in this project.
Maximum number of contracts allowed in this project.
Resource controls associated with tasks include the following:
Maximum CPU time (seconds) available to this task's processes.
Maximum number of LWPs simultaneously available to this task's processes.
Maximum number of process table slots simultaneously available to this task's processes.
Note - Both normal processes and zombie processes take up process table slots. The max-processes resource control thus protects against zombie processes exhausting the process table. Note that max-lwps cannot protect against zombie processes exhausting the process table since zombie processes do not have any LWPs by definition.
Resource controls associated with processes include the following:
Maximum amount of address space (bytes), as summed over segment sizes, available to this process.
Maximum size (bytes) of a core file that is created by this process.
Maximum CPU time (seconds) available to this process.
Maximum file descriptor index that is available to this process.
Maximum file offset (bytes) available for writing by this process.
Maximum number of messages on a message queue. This value is copied from the resource control at msgget() time.
Maximum number (bytes) of messages on a message queue. This value is copied from the resource control at msgget() time. When you set a new project.max-msg-qbytes value, initialization occurs only on the subsequently created values. The new project.max-msg-qbytes value does not effect existing values.
Maximum number of semaphores allowed for a semaphore set.
Maximum number of semaphore operations that are allowed for a semop() call. This value is copied from the resource control at msgget() time.A new project.max-sem-ops value only affects the initialization of subsequently created values and has no effect on existing values.
Maximum number of events that are allowed per event port.
Zone-wide resource controls are available on a system with zones installed. Zone-wide resource controls limit the total resource usage of all process entities within a zone.
Absolute limit on the amount of CPU resources that can be consumed by a non-global zone. A value of 100 means 100 percent of one CPU as the project.cpu-cap setting. A value of 125 is 125 percent, because 100 percent corresponds to one full CPU on the system when using CPU caps.
Limit on the number of fair share scheduler (FSS) CPU shares for a zone. The scheduling class must be FSS. CPU shares are first allocated to the zone, and then further subdivided among projects within the zone as specified in the project.cpu-shares entries. A zone with a higher number of zone.cpu-shares is allowed to use more CPU than a zone with a low number of shares.
Total amount of physical locked memory available to a zone.
Maximum number of lofi devices that can be created by a zone.
Maximum number of LWPs simultaneously available to this zone
Maximum number of message queue IDs allowed for this zone
Maximum number of process table slots simultaneously available to this zone
Note - The zone.max-processes resource control enhances resource isolation by preventing a zone from using too many process table slots and thus affecting other zones. The allocation of the process table slots resource across projects within the zone can be controlled by using the project.max-processes resource control. The global property name for this control is max-processes. The zone.max-processes resource control can also encompass the zone.max-lwps resource control. If zone.max-processes is set and zone.max-lwps is not set, then zone.max-lwps is implicitly set to 10 times the zone.max-processes when the zone is booted.
Both normal processes and zombie processes take up process table slots. The max-processes resource control thus protects against zombie processes exhausting the process table. Note that max-lwps cannot protect against zombie processes exhausting the process table since zombie processes do not have any LWPs by definition.
Maximum number of semaphore IDs allowed for this zone
Maximum number of shared memory IDs allowed for this zone
Total amount of shared memory allowed for this zone
Total amount of swap that can be consumed by user process address space mappings and tmpfs mounts for this zone.
For more information, see Zone-Wide Resource Controls in Oracle Solaris 11.1 Administration: Oracle Solaris Zones, Oracle Solaris 10 Zones, and Resource Management.
For information on configuring zone-wide resource controls, see Chapter 16, Non-Global Zone Configuration (Overview), in Oracle Solaris 11.1 Administration: Oracle Solaris Zones, Oracle Solaris 10 Zones, and Resource Management and Chapter 17, Planning and Configuring Non-Global Zones (Tasks), in Oracle Solaris 11.1 Administration: Oracle Solaris Zones, Oracle Solaris 10 Zones, and Resource Management.
Note that it is possible to use the zonecfg command to apply a zone-wide resource control to the global zone on a system with non-global zones installed. Also note that setrctl(2) will only succeed when called as a privileged user in the global zone. Inside a non-global zone, root cannot set zone-wide resource controls.
For each threshold value that is placed on a resource control, the following restricted set of signals is available:
Terminate the process.
Signal generated by resource control facility when the resource control limit is exceeded.
When carrier drops on an open line, the process group that controls the terminal is sent a hangup signal, SIGHUP.
Job control signal. Stop the process. Stop signal not from terminal.
Terminate the process. Termination signal sent by software.
Terminate the process. Kill the program.
Terminate the process. File size limit exceeded. Available only to resource controls with the RCTL_GLOBAL_FILE_SIZE property.
Terminate the process. CPU time limit exceeded. Available only to resource controls with the RCTL_GLOBAL_CPUTIME property.
Other signals might be permitted due to global properties of a specific control.
Note - Calls to setrctl() with illegal signals fail.
Figure 5-2 Setting Privilege Levels for Signals