| Skip Navigation Links | |
| Exit Print View | |
|
Managing SMB File Sharing and Windows Interoperability in Oracle Solaris 11.1 Oracle Solaris 11.1 Information Library |
| Skip Navigation Links | |
| Exit Print View | |
|
Managing SMB File Sharing and Windows Interoperability in Oracle Solaris 11.1 Oracle Solaris 11.1 Information Library |
1. Sharing Files Between Windows and Oracle Solaris Systems
Configuring the SMB Server - Process Overview
Utilities and Files Associated With the SMB Server and Client
Authentication, Directory, Naming, and Time Services
Host-Based Access Control to SMB Shares
Access Control Lists on SMB Shares
SMB Autohome Map Key Substitution
Client-Side Caching for Offline Files
SMB Share Execution Properties
SMB Support for the Distributed File System
2. Setting Up Identity Mapping Between Windows and Oracle Solaris Systems
3. Setting Up a Oracle Solaris SMB Server to Manage and Share Files
The Oracle Solaris operating system (Oracle Solaris OS) has reached a new level of Windows interoperability with the introduction of an integrated SMB server. An Oracle Solaris server can now be an active participant in a Windows active directory domain and provide ubiquitous, cross-protocol file sharing through SMB and NFS to clients in their native dialect.
The SMB server allows a native Oracle Solaris system to serve files, by means of SMB shares, to SMB enabled clients, such as Windows and Mac OS systems. A Windows client (or other SMB client) can interoperate with the SMB server as it would with a Windows server.
An SMB server can operate in either workgroup mode or in domain mode. In workgroup mode, the SMB server is responsible for authenticating users locally when access is requested to shared resources. This authentication process is referred to as local login. In domain mode, the SMB server uses pass-through authentication, in which user authentication is delegated to a domain controller.
When a user is successfully authenticated, the SMB server generates an access token using the security identifiers (SIDs) that represent the user's identity and the groups of which the user is a member. When the user requests access to files or resources from the server, the access token is used to determine access to files by cross-checking the token with the access control list (ACL) or permissions on files and resources. Oracle Solaris OS credentials have been enhanced to fully support Windows-style SIDs. In addition, file systems, such as the ZFS file system, support Windows-style ACLs and access checking.
The Oracle Solaris OS is unique in that it can manage user identities simultaneously by using both traditional UIDs (and GIDs) and SIDs. When a user is authenticated through the SMB server, the user's SMB identity is mapped to the appropriate UNIX or Network Information Service (NIS) identity by using the idmap identity mapping service. If an existing UNIX or NIS identity exists, that identity is used. Otherwise, a temporary identity is generated using ephemeral UIDs and GIDs, as required. Ephemeral IDs are valid only within each Oracle Solaris OS instance and only until the system is rebooted. These IDs are never stored on disk or transmitted over the network. When an ACL is stored on disk through the SMB server, the SIDs are used to generate the access control entries. Oracle Solaris utilities, such as ls and chmod, support ACL management.
For more information about how the Oracle Solaris OS manages user identities, see Chapter 2, Setting Up Identity Mapping Between Windows and Oracle Solaris Systems.
The following diagram shows how an Oracle Solaris file server can operate simultaneously with both NIS and Windows domains. The Windows domain controller provides SMB authentication and naming services for SMB clients and servers, while the NIS servers provide naming services for NFS clients and servers.
Figure 1-1 SMB Environment
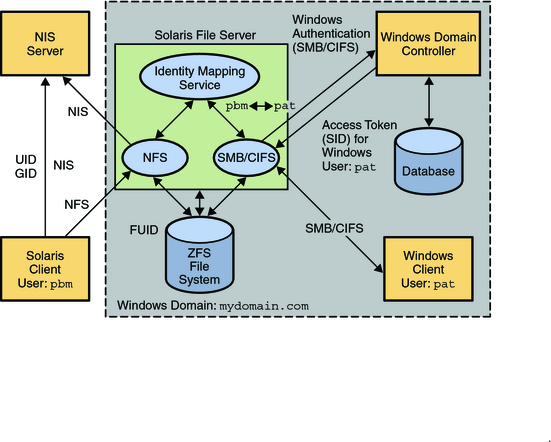
The Oracle Solaris services described in this book include the following components:
For a high-level overview of configuring the SMB server, see Configuring the SMB Server - Process Overview. For information about configuring the server, see Chapter 3, Setting Up a Oracle Solaris SMB Server to Manage and Share Files. For more information about the SMB server, see the smbadm(1M), smbd(1M), smbstat(1M), smb(4), smbautohome(4), and pam_smb_passwd(5) man pages.
The SMB features offered by the Oracle Solaris service depend on the file system being shared. To fully support the SMB server, a file system should support the following features:
If the file system supports the archive, hidden, read-only, and system attributes, these attributes are made available as the DOS attributes available on Windows systems. The ZFS file system supports these attributes.
If the file system supports Oracle Solaris extended attributes, they are made available as NTFS alternate data streams.
The case-sensitivity capabilities of the file system are made available to SMB clients. To support both Windows-style access and POSIX access, a file system should support mixed-mode, which is simultaneous support for case-sensitive and case-insensitive name operations.
The Oracle Solaris OS supports both the NFS and SMB protocols, which have different expectations regarding case behavior. For instance, Windows clients typically expect case-insensitive behavior while local applications and NFS clients typically expect case-sensitive behavior. The ZFS file system supports three case modes: case-sensitive, case-insensitive, and mixed. The ZFS file system can indicate case conflicts when in mixed mode. Use mixed mode for maximum multi-protocol compatibility. This mode is enabled by default on ZFS file systems.
To provide full Windows access control list (ACL) support, file systems should be able to store SIDs and they should at least support NFSv4 ACLs.
Note - Samba and SMB servers cannot be used simultaneously on a single Oracle Solaris system. The Samba server must be disabled in order to run the SMB server. For more information, see How to Disable the Samba Service.
For information about the supported features of the UFS and ZFS file systems, see the ufs(7FS) man page and the Oracle Solaris 11.1 Administration: ZFS File Systems, respectively.
For information about how to access SMB shares from your client, refer to the client documentation.
By using the SMB client, a user can mount remote SMB shares (directories) on his Oracle Solaris system to get read-write access to previously inaccessible files. The SMB client does not include the ability to print by means of SMB or the ability to access SMB resources other than files and directories. The SMB client enables an unprivileged user to mount and unmount shares on directories he owns.
For more information about how to use the SMB client to access shares, see Chapter 4, Using SMB File Sharing on Client Systems, and the mount_smbfs(1M), smbadm(1M), smb(4), pam_smbfs_login(5), and smbfs(7FS) man pages.
The Oracle Solaris OS includes an identity mapping service that enables you to map identities between Oracle Solaris systems and Windows systems.
This identity mapping service supports the following types of mappings between Windows security identities (SIDs) and Oracle Solaris user IDs and group IDs (UIDs and GIDs):
Directory-based mapping. If configured, the idmap service attempts to use mapping information that is stored in a directory with other user or group information.
Directory-based name mapping. Uses name mapping information that is stored in user or group objects in the Active Directory (AD), the native LDAP directory service, or both, to map users and groups.
Identity Management for UNIX (IDMU) directory mapping. Uses UID and GID information stored in the AD data for the Windows user or group. IDMU is an optional AD component that was introduced in Windows Server 2003R2.
Rule-based mapping. Uses idmap rules to map Windows and Oracle Solaris users and groups by name.
Ephemeral ID mapping. A UID or GID is dynamically allocated as needed for every SID that is not already mapped by name. Ephemeral ID mapping is used by default.
The idmap command can be used to create and manage the name-based mappings and to monitor the mappings in effect.
For more information about mapping user and group identities, see Mapping User and Group Identities. For information about how to determine your identity mapping strategy, see Creating Your Identity Mapping Strategy. For instructions on how to use the idmap command, see Managing Directory-Based Name Mapping for Users and Groups (Task Map), Managing Rule-Based Identity Mapping for Users and Groups (Task Map), and the idmap(1M) man page.
The SMB server and the SMB client use the sharectl command to manage configuration properties. For descriptions of the SMB client and server properties, see the sharectl(1M) and smb(4) man pages.
The SMB properties and their values are stored in the Service Management Facility (SMF). For more information about SMF, see Chapter 6, Managing Services (Overview), in Oracle Solaris Administration: Common Tasks.
The sharectl command is used throughout the configuration process to set and view properties. This command and examples of its use are described in Chapter 3, Setting Up a Oracle Solaris SMB Server to Manage and Share Files and Chapter 4, Using SMB File Sharing on Client Systems.