| Skip Navigation Links | |
| Exit Print View | |
|
Trusted Extensions User's Guide Oracle Solaris 11.1 Information Library |
| Skip Navigation Links | |
| Exit Print View | |
|
Trusted Extensions User's Guide Oracle Solaris 11.1 Information Library |
1. Introduction to Trusted Extensions
2. Logging In to Trusted Extensions (Tasks)
3. Working in Trusted Extensions (Tasks)
Visible Desktop Security in Trusted Extensions
Trusted Extensions Logout Process
How to Lock and Unlock Your Screen
How to Log Out of Trusted Extensions
How to View Your Files in a Labeled Workspace
How to Access the Trusted Extensions Man Pages
How to Access Initialization Files at Every Label
How to Interactively Display a Window Label
How to Perform Some Common Desktop Tasks in Trusted Extensions
How to Change Your Password in Trusted Extensions
How to Log In at a Different Label
How to Allocate a Device in Trusted Extensions
How to Deallocate a Device in Trusted Extensions
How to Assume a Role in Trusted Extensions
How to Change the Label of a Workspace
How to Add a Workspace at Your Minimum Label
How to Switch to a Workspace at a Different Label
How to Move a Window to a Different Workspace
How to Determine the Label of a File
How to Move Data Between Windows of Different Labels
How to Upgrade Data in a Multilevel Dataset
How to Downgrade Data in a Multilevel Dataset
 | Caution - If the trusted stripe is missing from your workspace, contact the security administrator. The problem with your system could be serious. The trusted stripe must not appear during login, or when you lock your screen. If the trusted stripe shows, contact the administrator immediately. |
If you leave your workstation briefly, lock the screen.
Figure 3-1 Lock Screen Selection
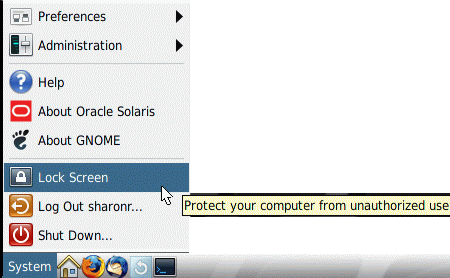
The screen turns black. At this point, only you can log in again.
Note - The trusted stripe must not appear when the screen is locked. If the stripe does appear, notify the security administrator immediately.
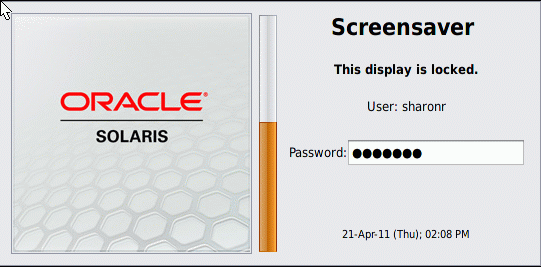
If the Screensaver dialog box does not appear, press the Return key.
This action returns you to your session in its previous state.
At most sites, the screen automatically locks after a specified period of idleness. If you expect to leave the workstation for awhile, or if you expect someone else to use your workstation, log out.
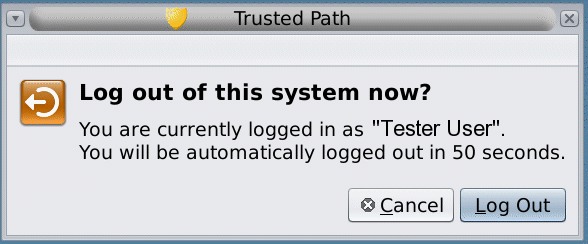
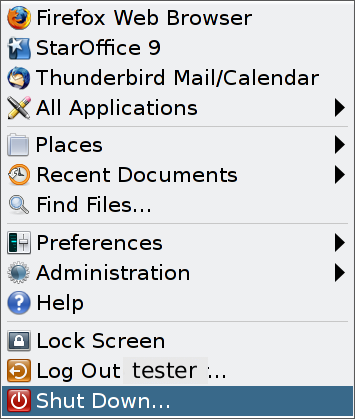
Logging out is the normal way to end a Trusted Extensions session. Use the following procedure if you need to turn off your workstation.
Note - If you are not on the console, you cannot shut down the system. For example, VNC clients cannot shut down the system.
Before You Begin
You must be assigned the Maintenance and Repair rights profile.
Confirm the shutdown.
To view your files, you use the same applications that you would use on your desktop on an Oracle Solaris system. If you are working at multiple labels, only the files that are at the label of the workspace are visible.
Click mouse button 3 over the background. From the menu, choose Open Terminal.
The folder opens in a File Browser. The File Browser application opens at the same label as the current workspace. The application provides access to only those files that are at its label. For details about viewing files at different labels, see Containers and Labels. To view files at different labels in one workspace, see How to Move a Window to a Different Workspace.
% man trusted_extensions
For a list of user commands that are specific to Trusted Extensions, see Appendix D, List of Trusted Extensions Man Pages, in Trusted Extensions Configuration and Administration. The man pages are also available from Oracle's documentation web site.
Linking a file or copying a file to another label is useful when you want to make a file with a lower label visible at higher labels. The linked file is only writable at the lower label. The copied file is unique at each label and can be modified at each label. For more information, see .copy_files and .link_files Files in Trusted Extensions Configuration and Administration.
Before You Begin
You must be logged in to a multilevel session. Your site's security policy must permit linking.
Work with your administrator when modifying these files.
Type your entries one file per line. You can specify paths to subdirectories in your home directory, but you cannot use a leading slash. All paths must be within your home directory.
Copying an initialization file is useful when you have an application that always writes to a file with a specific name, and you need to separate the data at different labels.
Type your entries one file per line. You can specify paths to subdirectories in your home directory, but you cannot use a leading slash. All paths must be within your home directory.
Example 3-1 Creating a .copy_files File
In this example, the user wants to customize several initialization files per label. In her organization, a company web server is available at the Restricted level. So, she sets different initial settings in the .mozilla file at the Restricted level. Similarly, she has special templates and aliases at the Restricted level. So, she modifies the .aliases and .soffice initialization files at the Restricted level. She can easily modify these files after creating the .copy_files file at her lowest label.
% vi .copy_files # Copy these files to my home directory in every zone .aliases .mozilla .soffice
Example 3-2 Creating a .link_files File
In this example, the user wants her mail defaults and C shell defaults to be identical at all labels.
% vi .link_files # Link these files to my home directory in every zone .cshrc .mailrc
Troubleshooting
These files do not have safeguards for dealing with anomalies. Duplicate entries in both files or file entries that already exist at other labels can cause errors.
This operation can be useful to identify the label of a partially hidden window.
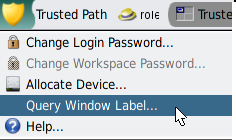
The label for the region under the pointer is displayed in a small rectangular box at the center of the screen.
Figure 3-2 Query Window Label Operation
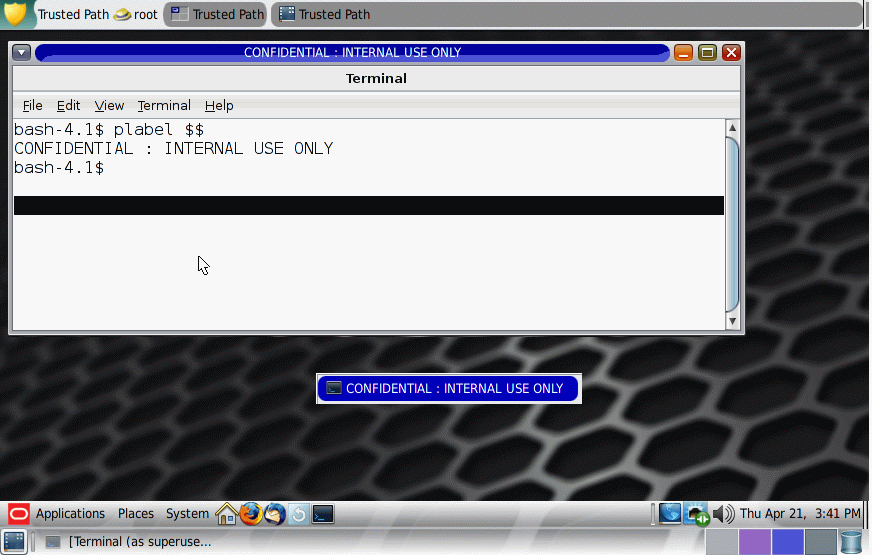
An untrusted application can gain control of the keyboard or mouse pointer. By finding the pointer, you can regain control of the desktop focus.
Press the keys simultaneously to regain control of the current desktop focus. On the Sun keyboard, the diamond key on either side of the spacebar is the Meta key.
If the grab of the keyboard or mouse pointer is not trusted, the pointer moves to the trusted stripe. A trusted pointer does not move to the trusted stripe.
Example 3-3 Forcing the Mouse Pointer to the Trusted Stripe
In this example, a user is not running any trusted processes but cannot see the mouse pointer. To bring the pointer to the center of the trusted stripe, the user presses the Meta-Stop keys simultaneously.
Example 3-4 Finding the Real Trusted Stripe
On a multiheaded Trusted Extensions system whose monitors are configured to display a separate desktop on each monitor, a user sees one trusted stripe per monitor. Therefore, a program other than Trusted Extensions is generating a trusted stripe. Only one trusted stripe displays when a multiheaded system is configured to display a separate desktop per monitor.
The user halts work and immediately contacts the security administrator. Then, the user finds the real trusted stripe by placing the mouse pointer in an untrusted location, such as over the workspace background. When the user presses the Alt-Break keys simultaneously, the pointer moves to the trusted stripe that is generated by Trusted Extensions.
Some common tasks are affected by labels and security. In particular, the following tasks are affected by Trusted Extensions:
Emptying the trash
Finding calendar events
Click mouse button 3 over the Trash Can icon on the desktop. Choose Empty Trash, then confirm.
Note - The trash can contains files only at the label of the workspace. Delete sensitive information as soon as the information is in the trash can.
Calendars show only the events at the label of the workspace that opened the calendar.
You can customize the workspace configuration for every label at which you log in.
Note - Users can save desktop configurations. Roles cannot save desktop configurations.
Your desktop is restored in this configuration when you next log in at this label.